Aice Global Solutions delivers a comprehensive cybersecurity framework designed to secure every aspect of your business. Our services encompass regulatory compliance, in-depth security audits, risk assessments, and advanced threat detection and response.

Aice Global is a leading international Risk Management and Information Security corporation, dedicated to delivering cutting-edge cybersecurity solutions tailored to meet the evolving needs of modern enterprises. With a mission to help organizations stay secure in an increasingly complex digital world, we offer a broad portfolio of services including Information Security Auditing, Vulnerability Assessment, Penetration Testing (VAPT), Network Security, Cloud Security, and Continuous Security Advisory Feeds.
Our company is spearheaded by a team of seasoned management professionals, cybersecurity strategists, and technology visionaries who bring decades of expertise and industry insight. This leadership foundation allows Aice Global to provide clients with a comprehensive, proactive, and results-driven approach to tackling cybersecurity risks and compliance challenges.
At Aice Global Solutions, we offer a wide range of advanced technology and security services designed to help organizations thrive in today’s fast-paced digital environment. Our solutions are tailored to meet the specific needs of each client, ensuring maximum effectiveness, scalability, and value. Below is an overview of the core services we provide



Aice Global enables organizations to maximize the value of their security awareness programs without burdening internal IT or administrative teams. We take care of the heavy lifting, so you can focus on what matters most—your business.
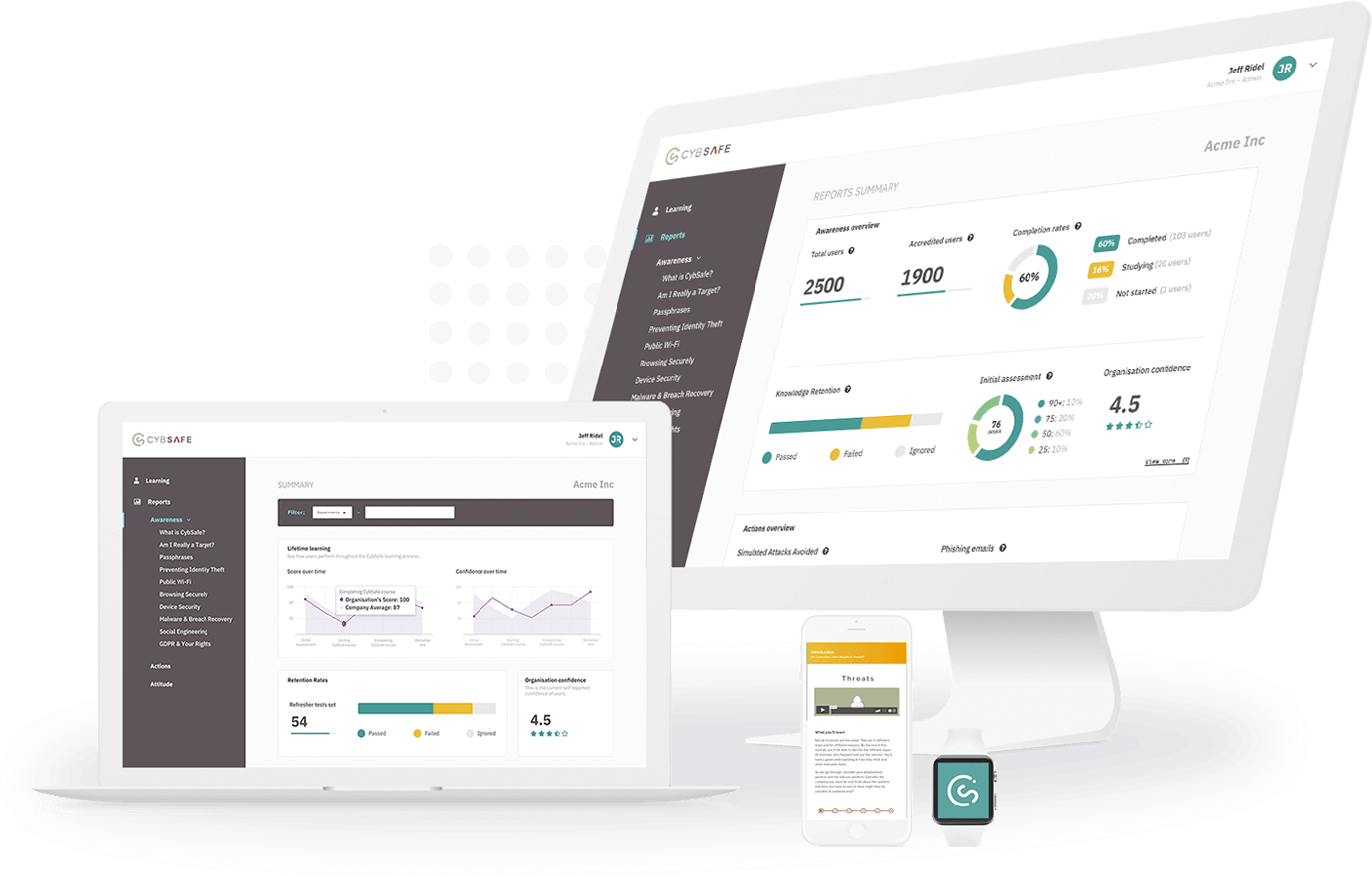





We collaborate with top-tier market leaders in the cybersecurity industry to deliver best-in-class products and technologies. These strategic partnerships enable us to provide our clients with cutting-edge, reliable, and scalable cybersecurity solutions tailored to their unique needs.
Salt Security provides advanced API security by using AI to detect threats, prevent attacks, and protect sensitive data, ensuring safe and reliable API usage.
Orca Security provides comprehensive cloud security by detecting risks and vulnerabilities across cloud workloads instantly.
Zscaler provides cloud-based security, enabling fast, secure internet access and zero trust network protection.
Invicti delivers automated web application security scanning to identify and remediate vulnerabilities efficiently.
It is a long established fact that a reader will be distracted by the readable content of a page when looking at its layout.
It is a long established fact that a reader will be distracted by the readable content of a page when looking at its layout. The point of using Lorem Ipsum is that it has a more-or-less normal distribution of letters, as opposed to using 'Content here, content here', making it look like readable English.

It is a long established fact that a reader will be distracted by the readable content of a page when looking at its layout. The point of using Lorem Ipsum is that it has a more-or-less normal distribution of letters, as opposed to using 'Content here, content here', making it look like readable English.

It is a long established fact that a reader will be distracted by the readable content of a page when looking at its layout. The point of using Lorem Ipsum is that it has a more-or-less normal distribution of letters, as opposed to using 'Content here, content here', making it look like readable English.

It is a long established fact that a reader will be distracted by the readable content of a page when looking at its layout. The point of using Lorem Ipsum is that it has a more-or-less normal distribution of letters, as opposed to using 'Content here, content here', making it look like readable English.

It is a long established fact that a reader will be distracted by the readable content of a page when looking at its layout. The point of using Lorem Ipsum is that it has a more-or-less normal distribution of letters, as opposed to using 'Content here, content here', making it look like readable English.

It is a long established fact that a reader will be distracted by the readable content of a page when looking at its layout. The point of using Lorem Ipsum is that it has a more-or-less normal distribution of letters, as opposed to using 'Content here, content here', making it look like readable English.

Aice Global Solutions specializes in delivering best-in-class security services tailored to meet your unique business needs.
Our expert team ensures comprehensive protection through customized, industry-leading cybersecurity solutions designed to safeguard your digital environment.
Receive practical guidance to enhance your cybersecurity and risk management, along with a clear roadmap to close security gaps effectively.
Aice Global’s Cybersecurity Practice identifies and closes security gaps, reducing risk and building a resilient defense against evolving threats.
The first 72 hours after discovering a breach are crucial and can greatly affect your organization’s resilience and long-term security.
We help organizations at every stage of their cyber resilience journey, offering flexible resources to meet evolving cybersecurity needs.
No matter where you are in your security journey—Start with a FREE assessment and take the first step toward stronger cybersecurity.